What is Two Factor Authentication (2FA) and Why Do I Need it? Sounds like a Bunch of Jargon
What is Two Factor Authentication (2FA) and Why Do I Need it? Sounds like a Bunch of Jargon.
If the early days of the internet are remembered for the proliferation of spam, pop-up advertisements, and ‘You’ve Got Mail’ - the modern internet has ushered in a new age of cyber threats. A time where personal information is a commodity with value. 2FA also known as two factor authentication is an added layer of protection that is fast becoming standard practice to safeguard your most sensitive online accounts. If you use any online services that require you to log in with an username and password (e.g. email, social media, online banking etc.), then you should be using Two Factor authentication wherever possible. Why? Read on...
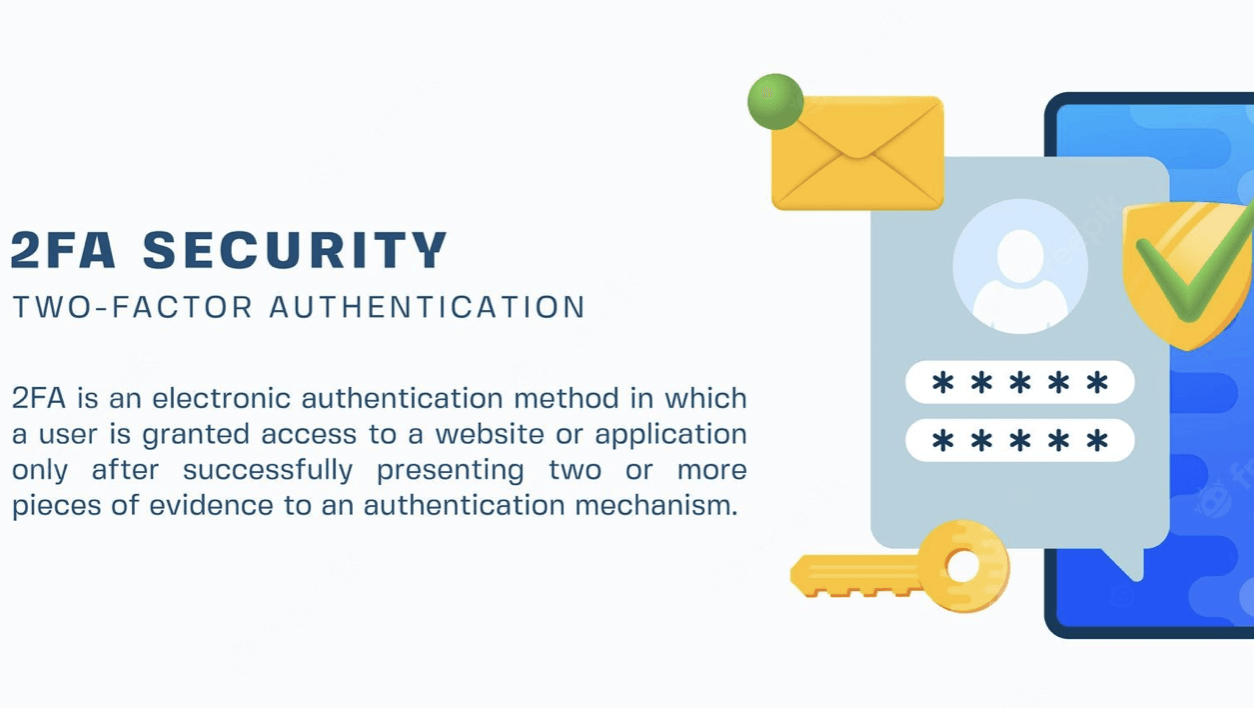
What is Two Factor Authentication?
Two factor authentication (2FA), also known as multi-factor authentication, is an added layer of protection when logging into your accounts. Traditionally, when logging into your online accounts, you will only need to provide your login details (username and password). With 2FA enabled, you will have to provide your login details plus an additional piece of information from a second category. The first category will be something you know (e.g. your login details), while the second will be something you have. We’ll delve into the types of second factors shortly. Before we get into the nitty gritty of how two factor authentication works, it is important to understand why it is used in the first place. Traditional user names and passwords have long been a standard method of accessing accounts online. The problem, however, is that they are incredibly easy to hack.
Why is 2FA Important?
The fact of the matter is that passwords alone are not enough to keep your accounts secure. The unfortunate reality is that the majority of people are using unsafe passwords. If you are one of these people, then you are leaving your accounts open to being hacked. As such, you need to be taking steps to increase the security of your online accounts. One way to do this is to enable 2FA. A significant proportion of online services now offer 2FA as an added layer of security. It is important that you take advantage of this. While a password alone might be enough to keep certain low-risk accounts secure, you should be looking to use 2FA for your most sensitive accounts.
How Does 2FA Work?
The reason that 2FA is so effective is that it is a one-time use code that is not dependent on your password. If you were to somehow get your password hacked, the hacker wouldn’t be able to use the one-time use code. There are various types of 2FA, but the most common are: - SMS-based 2FA (and why you should be wary) - App-based 2FA using Google Authenticator - App-based 2FA using third party authenticators
SMS-based 2FA (and why you should be wary)
The first type of 2FA was the SMS-based variant. This is where a user receives a code via a text message to their phone. This was incredibly popular for a time, but there are a number of reasons why you might want to be wary. The main reason is that SMS messages are not as secure as you would expect. There have been countless instances of hackers gaining access to people’s texts and using that as a way of gaining access to their accounts. While this is less common in North America, it is incredibly common in other parts of the world. The way that hackers access people’s texts varies. The most common method is to call the service provider pretending to be the person in question. Once they are verified, they then request a new SIM card be sent to the person’s address. This new SIM card has the person’s phone number and is used to reset their account login details.
App-based 2FA using Google Authenticator
The most secure form of 2FA is arguably the app-based version using Google Authenticator. This app generates a one-time use code that changes every 30 seconds. This code will be used in conjunction with your login details to ensure that only you can access your account. There are a number of advantages to using Google Authenticator for 2FA. One of the most important is that there is no way for a hacker to gain access to the code. It is generated on the app itself and is only accessible to the person who has the app installed on their phone. Another advantage of using Google Authenticator for 2FA is that it is incredibly simple. You simply log in to your account as you normally would, input the code from the app, and you are good to go.
App-based 2FA using third party authenticators
While the Google Authenticator methods outlined above are effective, they do come with one drawback. That is, you must have your phone with you in order to log into your account. If you are like many people, you might not have your phone on you at all times (and are wary of leaving it unattended). This would therefore make it impossible to take advantage of the 2FA protection. Third party apps such as LastPass, 1Password, and Dashlane, offer the same level of protection as Google Authenticator, but they can be accessed from any device. This means that you can use your 2FA code to log into your account from any device, regardless of whether or not you have your phone with you.
Final Words: The Importance of 2FA
Two factor authentication is an important way to protect your online accounts. With 2FA enabled, hackers will have to have access to both your username and password as well as your 2FA code in order to gain access to your account. This makes it much harder for them to gain access. There’s no doubt that the internet is a wonderful source of information and connects people from all over the globe. Cybersecurity experts, however, are warning that the internet’s promise of convenience and connectivity also poses major threats to computer users’ privacy.
The main reason for this is that people often don’t take the necessary steps to protect their data online. Sadly, there are many people who don’t take online security seriously, and this results in devastating consequences. The good news, though, is that you don’t have to be one of these people. If you take the steps necessary to protect your online accounts, then you can enjoy the internet’s benefits while remaining secure.
Contact Us
Thank you for contacting us.
We will get back to you as soon as possible.
Oops, there was an error sending your message. Please try again later.
All Rights Reserved | Tommy House Studios
All logos and trademarks displayed are the property of their respective owners.
Website Design by Tommy House Studios | Powered by LaunchCMS.com